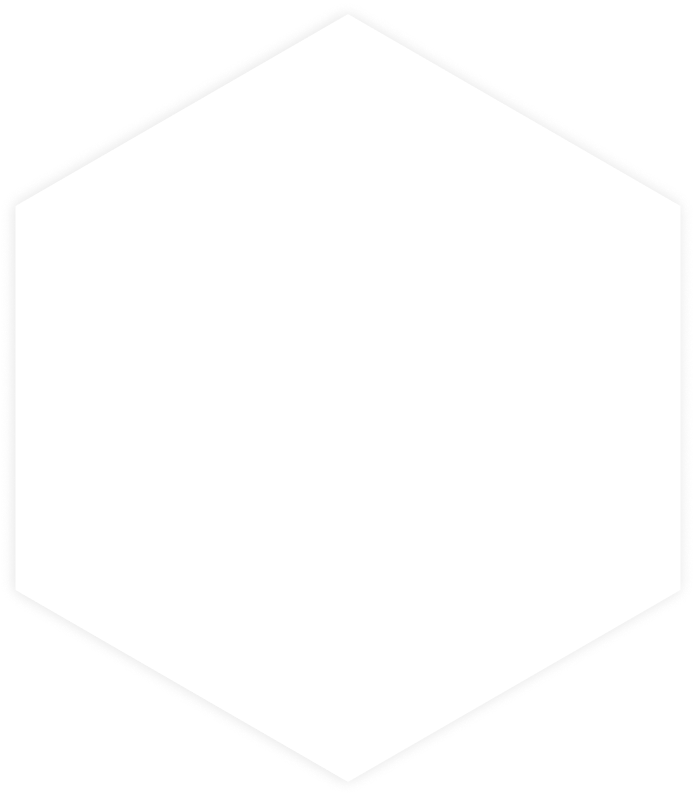
The 65,000-tonne HMS Queen Elizabeth, the Royal Navy’s largest ever warship, puts to sea for the first time, June 26, 2017. Photo: Royal Navy
When reporters were recently being given tours of the Royal Navy’s new “supercarrier,” HMS Queen Elizabeth, some were surprized to see a distinctive logo on several computer screens on the bridge and in control rooms. The logo was for Windows XP, the Microsoft computer operating system introduced in 2001. The ship itself was under construction for over eight years and the many of the procurement lead times were even longer. The reporters were told that the software was ordered in 2004, when XP was the latest and greatest version of the operating system.
Other than being slightly embarrassing that the brand new £3.5 billion aircraft carrier is running outdated software, why is this a problem? The problem is that the older operating systems are much more vulnerable to security breeches. In May, a worldwide ransomware attack was launched, which created havoc in networks in 99 counties around the world. (A new wave of ransomware cyber-attacks has hit within the last day. This time, port operations were also impacted, including Moller-Maersk and others.)
During the May attacks, the UK’s National Health Service (NHS) was hit very hard. Across Great Britain computer networks at at least 48 hospitals were shut down by the malware. How did the malware break into the networks? Most suspect it gained access through a flaw in Windows XP, which roughly 90% of British hospitals still use, to one extent or another.
Microsoft stopped supporting Windows XP in 2014 and they are clear about the risks of using the outdated system. On their page, “Windows XP support has ended,” they state: “If you continue to use Windows XP now that support has ended, your computer will still work but it might become more vulnerable to security risks and viruses.”
So, having an aircraft carrier whose networks have known cyber-security risks is a real concern, notwithstanding assurances from the Ministry of Defense that everything is under control.
On the other hand, there may be more to worry about than a hacked aircraft carrier. The British American Security Information Council (BASIC), a think-tank, recently released a paper titled, “Hacking UK Trident, a Growing Threat.” They discuss what they consider to be the increasing risk of a cyber-attack on the UK’s Vanguard-class submarines
armed with nuclear-tipped Trident II D-5 ballistic missiles.” The report’s Executive Summary begins:
A successful attack could neutralise operations, lead to loss of life, defeat or perhaps even trigger the catastrophic exchange of nuclear warheads (directly or indirectly). But the very possibility of cyber-attack and the growing capability to launch them against SSBNs, could have a severe impact upon the confidence of maintaining an assured second-strike capability and therefore on strategic stability between states. Recent suggestions that the fleet is vulnerable have sometimes been met with complacency and claims that the isolated ‘air-gapped’ systems cannot be penetrated. Whilst we recognize that it is important not to be alarmist, these claims are false.
The reference to the threat of “catastrophic exchange of nuclear warheads” is sufficiently alarming that one might overlook the statement that subs, while isolated and not often connected to networks, can indeed by hacked, at least according to the authors of the report. The Ministry of Defense has denied that such a vulnerability exists.
While not as scary as nukes or a hacked carrier, as merchant ships become more integrated into global networks, there is an increasing risk of cyber-attacks on ships at sea. In 2013, a group of researchers from the University of Texas demonstrated how a ship might be taken over remotely when they “spoofed” the GPS navigation system on the $80 million yacht, White Rose of the Drachs. The yacht captain had no idea that the boat’s GPS system was sending false information to the autopilot.
While spoofing GPS is scary, there could be far worse to come. Hackers on land have given us a hint of what could be possible. In 2015, two hackers took control of a standard Jeep Cherokee through its communications system. From roughly ten miles away, they remotely turned the windshield wipers on and off, blasted the air conditioning and took over control of the radio. Finally, they disabled the accelerator and shut the car down. Chrysler had to recall 1.4 million vehicles to fix the vulnerability.
Something similar could happen to a modern merchant ship. Imagine pirates taking control without having to climb boarding ladders. Just as the hackers carried off a remote-controlled car-jacking with the Jeep, it may be possible to take over a ship through “spoofed” navigation and hijacked bridge and engine controls. This seems unlikely, yet may not be completely far-fetched.
Networking and automation solve many problems but can also create new risks. As some ship owners work toward remote-controlled or even autonomous ships, these risks could increase dramatically. One day, guarding against cyber-attacks may be thought of as just as much a part of ship operations as avoiding collisions and keeping off the rocks.

 Join The Club
Join The Club