Crew Rescued In Red Sea After Attack On Ship Near Yemen
CAIRO, July 6 (Reuters) – The crew of a ship set on fire in an attack in the Red Sea on Sunday abandoned the vessel and were rescued as it took on water, a British maritime agency said, in...
by Tom Roberts, Maritime Analyst
Somali based pirates continue to cause serious challenges to merchant vessels transiting the Indian Ocean, and at the time of writing, EU NAVFOR statistics indicate that there are 26 vessels and 582 crew held captive off the coast of Somalia (not taking into account an unknown number of smaller dhows and fishing vessels that have been seized). Moreover, the International Maritime Bureau (IMB) reported that Somali pirates hijacked 49 vessels in 2010, an increase from 47 in 2009. With the use of hijacked mother ships, Somali pirates proved that they are capable of operating for extended periods of time in areas further out to sea; a trend that has continued in the first months of 2011.
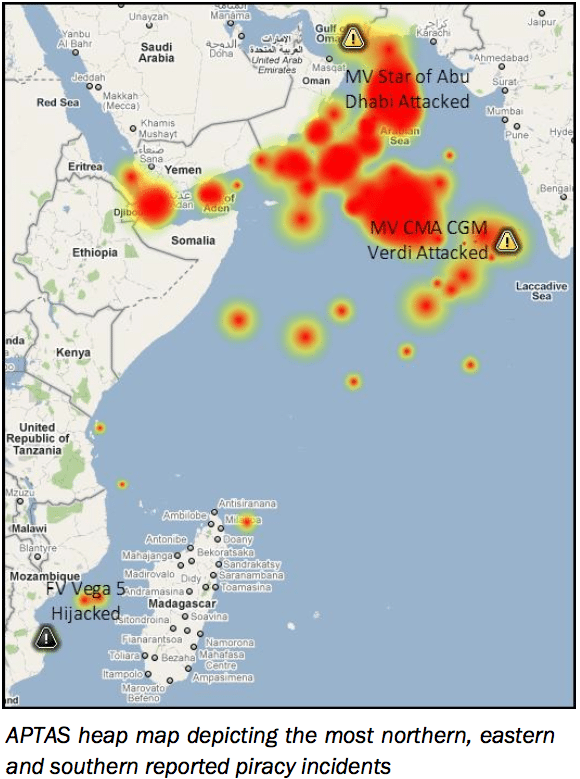
Although large mother ships enable pirates to operate at sea for longer periods of time, resulting in an extended sphere of operations, they also allow coalition forces in the region to track them. Throughout December 2010, it was assessed that there were eight mother ships operating in the region, allowing Somali pirates to record their most northern (25:01N – 060:26E), southern (21:55S – 035:36E) and eastern (09:25N – 073:02E) attacks.
The eastern and northern extents are not isolated incidents, but are part of a more recent migration into the Arabian Sea. The movement, illustrated on Drum Cussac‘s Automated Piracy Threat Assessment System (APTAS) heat map above, is unprecedented; in February 2010, there were only two documented incidents in the Arabian Sea.
The APTAS heat map, a valuable plotting tool when viewed over a number of days as the pattern and movement of attacks can be clearly charted, illustrates where the current focal point of activity lies. The reason for the movement into the region is twofold; it can be attributed to the utilisation of hijacked vessels as mother ships, allowing pirates to stay at sea for longer periods of time and to search for locally calmer sea states; but also to the success of the coalition forces in the Gulf of Aden, which has driven pirates to fresh hunting grounds.
Despite the documented elevation of piracy in areas that were previously free of piracy, pirates remain opportunistic and deploy to known shipping lanes to attack those vessels they deem to be vulnerable. There have been numerous documented incidents where a proactive response from the crew deterred pirates from boarding their vessel. This can be directed by the Master of the vessel, or sometimes by its onboard security team. In recent weeks and months there have also been incidents where pirates have boarded a vessel, but have been unable to gain control after the crew took refuge in a specially designed citadel. However, the experiences onboard MV Arrilah-I, which was boarded, but the pirates were unable to break into the citadel despite firing at it and pumping smoke in, need to be contrasted with those onboard MV Beluga Nomination, where the pirates were able to break into the citadel and take control of the vessel. The intensity of pirate attempts to break into the citadel on both occasions, amongst others, highlight the considerations that need to be taken into account when preparing a citadel, as well as the importance of seeking professional advice when doing so.
Forces operating in the region have reported that certain conditions must be met before naval assets would even consider a military response. These include, but are by no means limited to: 100% of the crew being in the citadel; they must have self-contained and independent two-way external communications; and the pirates must have no access to propulsion of the vessel.
Additionally, three days of provisions should be available within the citadel. On occasions when a naval frigate is close by, citadels have proved effective, and naval forces have been able to board a hijacked vessel, or their mere presence has resulted in voluntary abandonment by the pirates; however, as in the case of MV Beluga Nomination, given enough time and the appropriate tools, pirates have proved the ability to break into a citadel.
Although robust counter piracy measures have proved effective in deterring pirates, the area of a failed attack remains assessed as high-risk to subsequent attacks over the following hours, and any vessel transiting the region of a failed attack should exercise maximum caution. This is encapsulated in the APTAS chart below, which details five incidents over a one week period in January 2011, where a failed attack resulted in a subsequent attack shortly afterwards.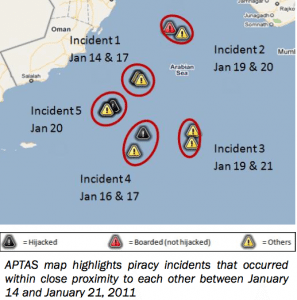
In conjunction with the documented elevation of piracy incidents, the amount of time hijacked vessels remain under pirate control has increased in the last year. The average number of days that the last five vessels to be released (MV EMS River, MV RAK Afrikana, MV York, MV Jahan Moni and MV Hannibal II) have spent under pirate control, is 153 days. The equivalent statistic for February 28, 2010 (accounting for vessels MV Navios Apollon, MV Pramoni, MV Maran Centaurus, MV De Xin Hai and MV Kota Wajar) is 63 days.
Although analysis of ransom payments is at best speculative (because of the secretive nature of the payments), anecdotal evidence suggests that these have also increased over recent years. A recent report into the financial cost of Somali piracy indicated that average ransom payments had increased from around $150,000 in 2005, to around $3.4m in 2009, and to around $5.4m in 2010. In addition, press sources have indicated that the largest ever ransom payment was made by Korean owners of MV Samho Dream, Samho Shipping, reported to be $9.5m on November 6, 2010.
However, the oversight of a large number of vessels anchored off Somalia presents constraints upon the logistical supply chain of pirate gangs, which in turn affects their profit. Press reports have indicated that some pirate groups have been willing to lower ransoms so as to release resources in order to carry out further hijackings, thereby raising turnover and generating more income. In the short-term, this attempt to generate a more economic business model‟ will create a speedier vessel turn-around‟; but may also lead to more vessels being targeted and attacked.
The presence of three naval task forces in the Indian Ocean has done little to reduce the threat of piracy, and two recent incidents have highlighted the scale of the challenge: Indian naval forces detained 61 pirates from a single mother ship operating in the Arabian Sea; and the recent hijacking of the general cargo ship, MV Sinar Kudus, was executed by between 30 and 50 pirates. Recognition of the scale of the problem, and the documented increase in pirate reach, has resulted in a hardening of attitudes towards armed teams amongst the shipping industry. In tacit support of such teams, the International Chamber of Shipping (ICS) clarified its stance, stating that the “ship operators must be able to retain all possible options available to deter attacks…” However, their use does not come without challenges. Even after approval from the vessel‟s insurers and flag state is gained, there are several issues that need to be deliberated when considering their use: the nexus of the relationship between the security team, the Master of the vessel and the owners of the vessel needs to be established; accountability and liability in the event of force being used should be considered; and all parties should be aware of the possibility of escalation in the use of force in potential future attacks.
A solution to the pervasive threat posed by pirates throughout the Indian Ocean must be sought through a coordinated approach that utilises the experiences of all of the stakeholders operating in the region. In conjunction with providing armed teams, the private industry is able to assist this process through more subtle methods. The contribution of comprehensive mapping and charting tools, in addition to analysis and intelligence provided by the private industry, plays an integral part in the initial transit planning phase. Moreover, the experience of a Vessel Protection Team (either armed or unarmed) that has completed multiple high-risk transits, gives an invaluable confidence boost to the Mariners aboard their vessel. Additionally, an embedded team acts not only as a bulwark against assaulting pirates, but also provides a visible deterrence and may prevent an attack occurring in the first instance.

Sign up for gCaptain’s newsletter and never miss an update

Subscribe to gCaptain Daily and stay informed with the latest global maritime and offshore news


Stay informed with the latest maritime and offshore news, delivered daily straight to your inbox
Essential news coupled with the finest maritime content sourced from across the globe.
Sign Up